Tag Archives: security protocols
The insider threat. 2023 Best
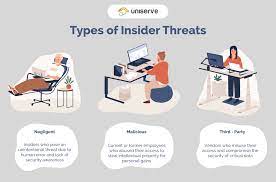
One of the most significant and common threats is the insider threat. What actions do you think is appropriate for security an organization regarding the insider threat? 2. Imagine you are the new CEO of a toy Research & Design Company.
The insider threat.
Paper instructions: 1. One of the most significant and common threats is the insider threat. What actions do you think is appropriate for security an organization regarding the insider threat? 2. Imagine you are the new CEO of a toy Research & Design Company. Your company was in the process of creating an electronic gaming toy and the final protocol plans have been developed. You are not sure what security protocols are in place. What is your approach for securing the data from an outside threat? Technical Requirements Your paper must be at a minimum of 2-3 pages per question for a total of 4-6 pages (the Title and Reference pages do not count towards the minimum limit).
The insider threat.
Scholarly and credible references should be used. A good rule of thumb is at least 2 scholarly sources per page of content. Type in Times New Roman, 12 point and double space. Students will follow the current APA Style as the sole citation and reference style used in written work submitted as part of coursework. Points will be deducted for the use of Wikipedia or encyclopedic type sources. It is highly advised to utilize books, peer-reviewed journals, articles, archived documents, etc. All submissions will be graded using the assignment rubric. https://youtu.be/pnEvMxXDqxM
Attached Files
|

 +1 650 405 4067
+1 650 405 4067

