Security Policy Implementation 2023 Best
Project: Security Policy Implementation Assignment Instructions: Overview For this assignment, review information assurance policy templates via the SANS policy template site and select a template of your choice, to be used as a GUIDE ONLY.
Security Policy Implementation
Project: Security Policy Implementation Assignment Instructions: Overview For this assignment, review information assurance policy templates via the SANS policy template site and select a template of your choice, to be used as a GUIDE ONLY. You can find this through Security Policy Templates found under Project: Security Policy Implementation Resources located on the Project: Security Policy Implementation Assignment page. DO NOT format your paper in this outline format! You can look at the General / Acceptable Encryption Policy to download either the doc or pdf file, but this is NOT how you will format your paper.
Security Policy Implementation
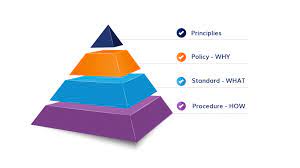
Utilize the downloaded template, from the SANS Policy website, and the Project Grading Rubric as a guide. However, you must still conform to the APA style of writing. I.E. DO NOT use the 4.1.1 outline style in your paper. You must use paragraph style and provide a 5-page write-up, highlighting key components that should be included during the development of an information assurance policy. These are your mandatory Level One headers: · Overview · Purpose · Scope · Policy Compliance · Related Standards · Definitions · Terms Instructions Discuss each component from the above list and the specific information that can be included within each section of the policy.
Security Policy Implementation
You will need at least 3 sentences under each Level One header. Support your paper with a minimum of five peer-review resources. In addition to these specified resources, other appropriate scholarly resources, including older articles, may be included. You are free to use as many other references as needed, as long as you have five peer-review sources properly included. Remember “scholarly articles” are the same as peer-review articles. Books, web sites, and blogs are not peer-review. Peer-review means a journal article that has been vetted by your peers. Books are allowed; however, they do not count as a peer-review article.
Security Policy Implementation
Length: Minimum of 5 full pages not including titles page(s) and reference pages Your paper should demonstrate thoughtful consideration of the ideas and concepts that are presented in the course and provide new thoughts and insights relating directly to this topic. Your response should reflect scholarly writing and current APA standards. Only one set of bullet points is allowed in this paper. The bullet points can be only for your ‘Related Terms’ section. No other bullet points/number points will be allowed. You must learn to phrase in sentence format. Please follow the Project: Security Policy Implementation Example.
Security Policy Implementation
Ask your professor if there are example papers from past courses for you to review for ideas. Please keep in mind that you will not have an Article Reference header at the top of the paper, but you will have a references section at the end. Be sure to have a title page with Running head, and do not use a real company or organization name, make one up. The purpose of this paper is to develop an information assurance policy. It should read like real guidance; you would deliver to your future or present company someday. The citations should be used to give clarity or credibility to a statement you are making.
Security Policy Implementation
Do not just cite something because you saw them say it that way or format their paper that way. Make a statement, then back it up with a citation from a scholarly source. Be sure to cover all that is described in the instructions for the assignment. It may be helpful to search the Jerry Falwell Library for scholarly sources that describe what is in an “Information Assurance Policy”, or “Information Security Plan” or “Information Security Policy.” You might also want to search in the library for “Information Assurance Policy “and “Security Plan” and look for relevant examples, but be careful to not copy/paste, cite all borrowed ideas and use scholarly sources for at least 5 of those citations.
Security Policy Implementation
Important APA format rules to follow: · You must have a correctly formatted Running head. · You can only have ONE direct quote in the paper. This direct quote must have a citation complete with a page number · You can only have one set of bullet points. This includes number points, as well. · Never use 1st person · Never use contractions · The above APA infractions will be counted off heavily! A note about the Level One headers: You cannot merge Level One headers. For example: Definitions and Terms. I must see a paragraph (3 sentences) under each Level One header. This is not acceptable: Terms – None. You must write a paragraph. Each Level One header must have verbiage. https://youtu.be/kh_4eTbezD8
Attached Files
|


 +1 650 405 4067
+1 650 405 4067

